that the personal data of about 820,000 students, past and present, had been breached from the program known as Skedula and Pupil Path, who attended NYC public schools going back to the year 2016. These programs were developed by NYC teachers, but are now owned by a company called Illuminate.
This was possibly the largest district breach in US history, according to Doug Levin, a data security expert who was quoted in the Daily News, (though this Pearson breach that affected multiple districts was larger.) There have also been articles in the NY Post and The Record about this hugely damaging breach.
According to these articles, Illuminate says that hackers gained access to the names, birthdays, race and ethnicities, home languages and ID numbers of current and former public-school students, going back to the 2016-17 school year, including in some cases, their disability and free lunch status as well.
If you are a parent whose children was
affected by the breach, or you suspect your children might have been; please
here is a sample message you can send to DOE to try to find out what data Illuminate had access to for your child. You can also reach out to us to let us know if you've heard anything from DOE or Illuminate about this, and/or email us info@studentprivacymatters.org with any questions.
This seems to have occurred during the program’s extended shutdown in January, which we wrote about at the time, speculating that it might have been caused by hackers and may be signalling a data breach. At that point, both DOE and Illuminate tried to tamp down concerns. As the DOE spokesperson was quoted by the NY Post at the time, “We’re in close communication with Illuminate Education as they investigate and have been informed that so far there is no confirmation any of our schools’ information was accessed or taken.”
The Post added: “The company did not explain or return messages from The Post, but emailed principals Friday it is transferring the data to a “new secured environment, ” implying that the data had not previously been sufficiently secured.
I was quoted in the Post that teachers often use the system to record very sensitive information about a student’s emotional state or behavior, and to recommend counseling or other intervention services. It is not clear at this point if those communications and records were breached as well.
Skedula was originally developed by NYC teachers, who started a company called Datacation that was later bought up by IO Education, which in turn was purchased by Illuminate Education. According to the NY Post, Illuminate has received more than $16 million from DOE in the last three years for the use of these programs. Abram Jiminez, who was hired by ex-Chancellor Carranza to lead a school improvement office, previously worked at Illuminate, and held stock in the company. He was later forced to quit after the conflict-of-interest was exposed, as well as other earlier scandals .
Now it turns out that not all the data held by Illuminate was properly encrypted, despite promises made by the vendor in their contractual agreements and as is required by the state student privacy law. Pertinent language from the NYS student privacy law Education Section 2D, passed in 2014, is excerpted below:
Many years ago, I submitted a FOIL request without success for all the privacy agreements that DOE had with vendors who had access to student personal information to see if these agreements complied with the state law. I re-submitted the FOIL request Sept. 2020, more than a year and a half ago.
After the breach late Friday, the DOE sent me a link to 960 pages of documents consisting of their privacy agreements with 19 vendors, including Illuminate. Though lengthy, this is far from a comprehensive list, considering DOE contracts with literally hundreds of ed tech vendors whose products they encourage schools to use.
The Illuminate privacy agreements I received are now posted here, along with my comments. They seem to require relatively strict security controls, including periodic risk assessments, a mutually agreed upon risk mitigation plan, the right for DOE to review all incidence response reports, and to request an SSAE16 report from the vendor (which I believe means a security audit.)
Moreover, Illuminate also “shall allow DOE, upon reasonable notice, to perform security assessments or audits of systems that handle or support Confidential Information. Such an assessment shall be conducted by an independent 3rd party agreed upon by the Vendor and the DOE.” In addition, vendors must engage an independent company to assess the security of their systems annually and produce audit logs for all systems that manage private information.
At this point, it is unclear if the vendor complied with any of these mandates, or if DOE ever asked them to do so, even after the January outage occurred.
In addition, the vendor was required to inform DOE of any suspected breach within 24 hours, instead of waiting for months, as they did in this case.
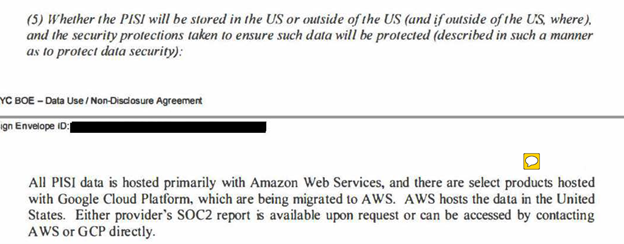
There is some evidence to suggest that the breach may have occurred when the data was being transferred to an Amazon cloud from a Google cloud. See pp. 34-35, for the question and response by Illuminate on the issue of where the personally identifiable student information (PISI) was stored:
This evasive language suggests that at least some of the data was initially stored on an insecure Google Cloud that was not in the US; though they did not answer the question of where it was located.
The following passage implies that migrating data "in bulk" is risky; and if this is attempted, it must be approved in advance by DOE InfoSec:
Did DOE approve of this data transfer? Did they ask any questions about the Google cloud, referenced above? If DOE did not do its due diligence to follow up on any of these issues, either when the contract was signed or especially after the January cyberattack occurred, it is nearly as much at fault as Illuminate.
There is also evidence from this document that DOE profoundly misunderstands FERPA, the primary federal law that protects privacy . They write the following:
And
yet actually, FERPA regulates the behavior of districts and schools, not
vendors.
Instead, DOE is responsible for limiting access to any and all student information that Illuminate did not need to perform its contractual obligations, including the highly sensitive student disability information and Free lunch status that ended up being hacked.
Also, the DOE should have made clear in the contract that all student data should be destroyed, not just when the contract lapsed, but annually, or at the very least, when students left the system, which clearly did not happen.
In any case, it
is clear from the law and these documents that the vendor can and should be
punished for delaying notification of this breach by as much as $8 million
dollars, as well as have its contract immediately revoked, and further fines
and possible criminal penalties imposed for lying about having encrypted the
data.
Chalkbeat ran an article yesterday about what parents can do to protect their kids from identify theft at this point. More advice here from JD Supra. Kids’ data is especially vulnerable to identity theft because they have no credit history, and current estimates are that this affects one in every 50 children, and costs families nearly $1 billion a year. Usually, districts or the vendors themselves sign up parents for free for services that are supposed to monitor identity theft– companies like Experian. Unfortunately, in order to sign up, parents have to provide them these companies more personal data, though these companies themselves experienced their own data breaches.
Sadly, there is really no recovering from the harm of having your child’s personal data spilled out on the internet. The most important lesson to take from this tragic incident is to make sure that DOE cleans up their act in the future by taking the following precautions:
1- DOE should minimize data sharing with third party vendors – instead of encouraging schools to sign up with hundreds of these data-gobbling ed tech companies, as they have done.
2- DOE should minimize the amount of personal data shared with each of their vendors, to restrict this disclosure to ONLY what the vendor needs to perform its contracted services, rather than give unlimited access, as seems to have happened here.
3- In their contracts, DOE should require that their vendors should be required to immediately delete student data annually from their records and certainly once the student has graduated.
4- DOE must provide rigorous oversight to ensure that their vendors perform and provide the independent security analyses, reporting, and audits required, including proof of encryption, and if they do not, cut them off immediately, fine them to the maximum, and cut off all future contracts.
5- Finally, the State Education Department should strictly enforce all the provisions in the state law, which still has not happened, despite the fact that the law was passed in 2014.
If you are a parent whose children was affected by the breach, or you suspect your children might have been; please here is a sample message you can send to DOE to try to find out what data Illuminate had access to for your child. You can also reach out to us at info@studentprivacymatters.org with any questions, and let let us know if you've heard anything from DOE or Illuminate about this.


No comments:
Post a Comment